The global security platform protecting what's important to you.
Protect your data, assets and people with confidence.
BioConnect delivers advanced Zero Trust authentication solutions, built with a Privacy by Design approach. Combat escalating cyber-physical security threats, meet evolving compliance standards, and scale with emerging technologies – all with BioConnect.
The global Trust Platform securing what's important to you.
Protect your data, assets and people with confidence.
BioConnect delivers advanced Zero Trust authentication solutions, built with a Privacy by Design approach. Combat escalating cyber-physical security threats, meet evolving compliance standards, and scale with emerging technologies – all with BioConnect.
The Gold Standard in Authentication
Still relying on outdated keycards and PINs?
Elevate your security with an AI-driven multi-modal authentication platform. Protect your data centers and facilities, prevent unauthorized access, and stay ahead of compliance requirements—all with BioConnect.

BioEntry W3
Advanced Facial Authentication Device with State-of-the-Art AI Technology.
Not sure which solution is for you?
Try our Solution Builder to create the perfect security solution for your needs.
Key Features
Automatic Enrollment
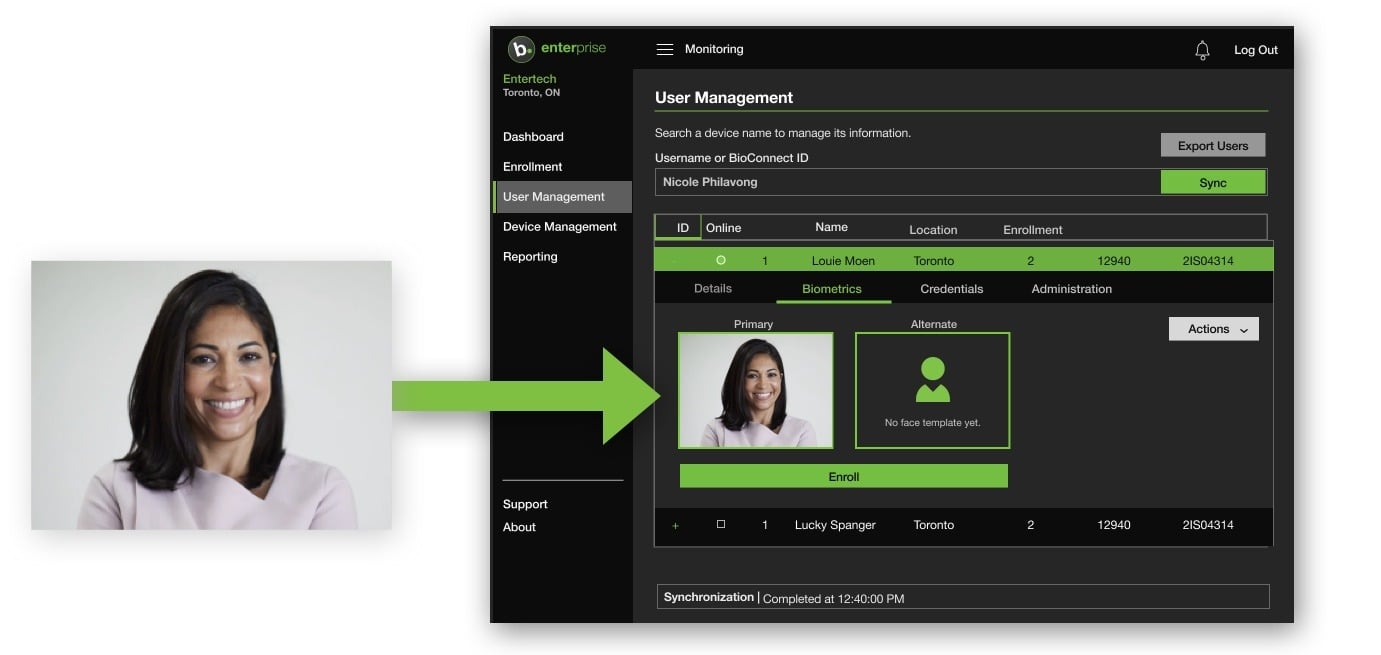
Automatic Biometric Enrollment
Eliminate onboarding friction with BioConnect's 'No Enrollment' feature, which securely syncs existing profile images for biometric authentication, ensuring compliance and efficiency from day one without requiring re-enrollment. BioConnect is proud to be the first and only solution on the market to offer this game-changing functionality.
Flexible Authentication

Flexible Authentication
BioConnect enhances authentication by offering a range of options beyond traditional biometrics, including digital mobile authenticators, mobile biometrics, mobile wallets, cards, and PINs. These solutions address exceptions without requiring additional hardware. As the first and only biometric provider to integrate digital mobile authentication platforms like DUO, Okta, PingID, SMS, and mobile biometrics for physical access, BioConnect sets a new standard for seamless and secure authentication.
Privacy & Compliance
Privacy & Compliance
Within the next three years most enterprises will be operating in jurisdictions that require consent from users before biometric enrollment, following in the footsteps of Europe (GDPR), Illinois (BIPA) and California (CCPA). Traditional point-to-point integrations can easily create gaps in your operational controls that can result in breaches and fines. BioConnect offers Consent Management to capture and track user consent for enrollment and use of biometric data in an auditable manner.
Seamless Integration

Certified, Scalable Integration to top PACS
Delivering certified compatibility with Physical Access Control Systems (PACS), BioConnect scales to support enterprise-wide deployments with centralized identity management at unmatched user and template volumes.
No rip-and-replace. BioConnect integrates seamlessly with your existing panels, readers and access control software. Multiple, different vendors? No problem.
Add biometrics to your existing system with BioConnect’s Enterprise Software. One person, one identity, across the enterprise. Integrates all locations, users and devices into one platform. Enroll and manage users entirely remotely.

Automatic Biometric Enrollment
Eliminate onboarding friction with BioConnect's 'No Enrollment' feature, which securely syncs existing profile images for biometric authentication, ensuring compliance and efficiency from day one without requiring re-enrollment. BioConnect is proud to be the first and only solution on the market to offer this game-changing functionality.

Flexible Authentication
BioConnect enhances authentication by offering a range of options beyond traditional biometrics, including digital mobile authenticators, mobile biometrics, mobile wallets, cards, and PINs. These solutions address exceptions without requiring additional hardware. As the first and only biometric provider to integrate digital mobile authentication platforms like DUO, Okta, PingID, SMS, and mobile biometrics for physical access, BioConnect sets a new standard for seamless and secure authentication.
Privacy & Compliance
Within the next three years most enterprises will be operating in jurisdictions that require consent from users before biometric enrollment, following in the footsteps of Europe (GDPR), Illinois (BIPA) and California (CCPA). Traditional point-to-point integrations can easily create gaps in your operational controls that can result in breaches and fines. BioConnect offers Consent Management to capture and track user consent for enrollment and use of biometric data in an auditable manner.

Certified, Scalable Integration to top PACS
Delivering certified compatibility with Physical Access Control Systems (PACS), BioConnect scales to support enterprise-wide deployments with centralized identity management at unmatched user and template volumes.
No rip-and-replace. BioConnect integrates seamlessly with your existing panels, readers and access control software. Multiple, different vendors? No problem.
Add biometrics to your existing system with BioConnect’s Enterprise Software. One person, one identity, across the enterprise. Integrates all locations, users and devices into one platform. Enroll and manage users entirely remotely.
More than access control.
BioConnect offers a fully integrated solution for your security, compliance, and efficiency needs.
Zero Trust Security Model
Our Security Platform provides a Zero Trust approach to security, ensuring that only authenticated individuals gain access to sensitive areas, data, and assets. By continuously verifying identity and requiring strict access controls, we mitigate risks and protect against both internal and external threats.
Privacy & Compliance-Driven
Stay ahead of stringent privacy regulations with features that capture user consent, manage biometric data in compliance with privacy standards, and automatically delete templates if consent is revoked. Our platform is built with privacy at its core, ensuring compliance with the latest data protection laws.
AI-Powered Biometric Authentication
Leverage the power of AI-driven facial recognition and biometric authentication. Our platform offers secure, frictionless access for users while adapting to evolving threats with sophisticated, context-based authentication options.
Seamless Integration
Designed for ease of deployment, our Security Platform integrates seamlessly with your existing identity and access control systems, such as Lenel, Genetec, AMAG, and others. Its API-driven architecture connects to a wide range of enterprise applications, enabling centralized identity management without disrupting your current infrastructure.
Multi-Modal / Multi-Factor Authentication
BioConnect integrates mobile multi-factor authentication options such as digital authenticators, mobile biometrics, and smart cards. These flexible solutions address edge cases and provide robust security even when biometrics alone aren’t feasible.
Scalable for the Future
As your business grows and technologies like AI, VR, and IoT evolve, our Security Platform scales to meet your needs. Whether you’re securing a single facility or a global network, BioConnect’s solutions are designed to expand and adapt as your requirements change.
What our customers say
"Deploying BioConnect was incredibly straightforward—within just 2 or 3 days, we had the system installed, running, and fully online. Whether you're working with Software House or another access control system, BioConnect is as close to plug-and-play as it gets—easier than any system I’ve encountered before. Everything just works seamlessly. Add to that their exceptional product quality and a team that’s genuinely great to work with, and it’s clear: BioConnect sets the standard. You simply can’t beat it."
"We chose BioConnect for several reasons, primarily the ability to integrate their system seamlessly with our system, but closely followed up by their feature set and quality of the [biometric readers] themselves. The almost immediate availability of the product – coupled with their excellent support – meant they really did stand out from the competition."
"Ensuring secure and efficient access across our numerous rooms and facilities is critical. BioConnect has completely transformed the way we manage access control. Their biometric devices provide us with unparalleled identity assurance while seamlessly integrating with our existing systems to create a unified and secure environment. Knowing that our facilities are protected with such reliable and advanced technology gives us peace of mind and the confidence to focus on what matters most—delivering exceptional care."
Securing the Future with AI-Powered Biometric Access Control
Get the free white paper on how access control is enhanced by the power of Artificial Intelligence.








