MOBILE AUTHENTICATION
Better experience.
Better security.
Eliminate the risk of stolen credentials and unauthorized access. The BioConnect Mobile Authenticator allows you to use your phone for secure authentication across doors, applications, networks, and cabinets—no keys or passwords required.
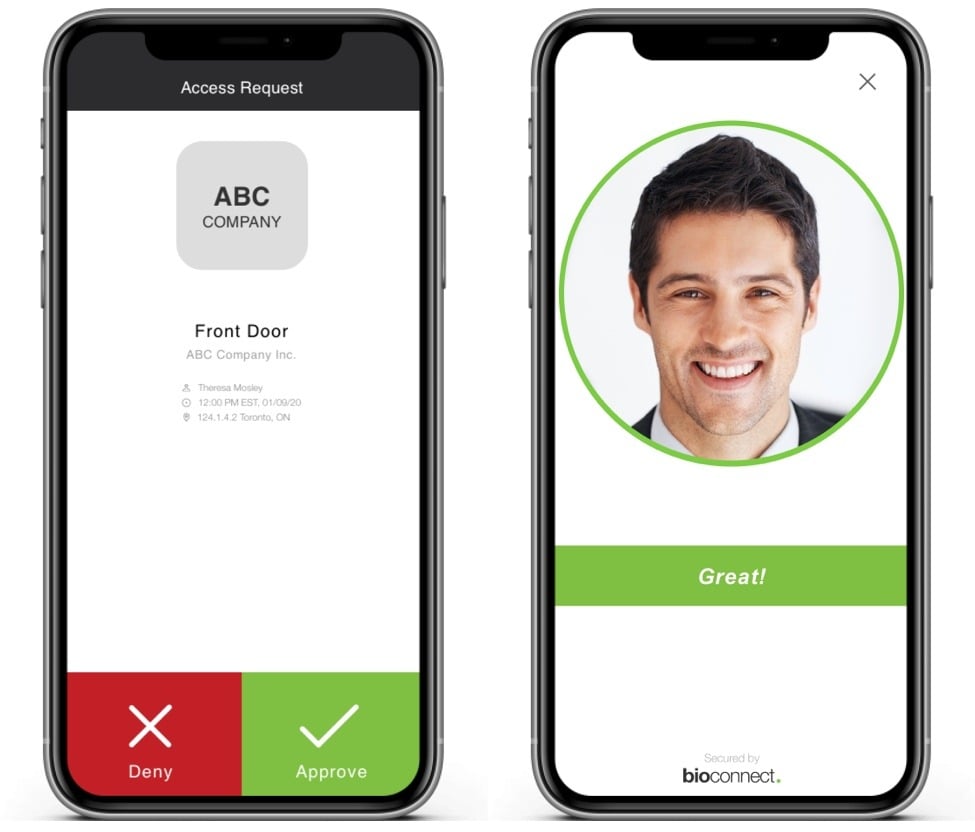
No More Stolen Credentials
Eliminate the risk of lost or stolen access cards with biometric authentication that verifies the person, not just the credential.
Frictionless, Mobile-First Security
Enable fast, secure authentication with a simple push notification or biometric approval—no more fumbling for cards or codes.
Unlock Your Doors and Desktop
From doors to digital applications, simplify your security into an, easy-to-use mobile solution for total access control.



Security that adapts to you, not the other way around.
Your workforce expects seamless access without compromising security. With BioConnect, you can implement biometric-powered mobile authentication that enhances security while making life easier.
Use Cases
Workforce Facility Access

Eliminate unauthorized access and streamline employee entry.
Traditional access cards can be cloned, stolen, or misplaced—leading to security vulnerabilities. With BioConnect Mobile Authenticator, employees can authenticate with their face or mobile approval, ensuring only the right people gain access while improving convenience.
Remote & Hybrid Work

Secure network, application, and VPN access from anywhere.
With more employees working remotely, traditional security measures fall short. BioConnect extends physical security to digital applications, ensuring that only verified employees can access critical company data—no matter where they are.
High-Security Areas

Secure your critical infrastructure and sensitive areas.
Data centers, R&D labs, and executive offices require trusted identity verification beyond keycards. BioConnect Mobile Authenticator offers biometric-based access control to prevent breaches and ensure compliance.
Healthcare Compliance

Meet stringent security regulations effortlessly.
Hospitals and pharmaceutical companies handle sensitive materials that require strict access control. BioConnect enables biometric authentication for restricted areas, helping organizations comply with HIPAA and other regulations while eliminating keycard-related risks.

Eliminate unauthorized access and streamline employee entry.
Traditional access cards can be cloned, stolen, or misplaced—leading to security vulnerabilities. With BioConnect Mobile Authenticator, employees can authenticate with their face or mobile approval, ensuring only the right people gain access while improving convenience.

Secure network, application, and VPN access from anywhere.
With more employees working remotely, traditional security measures fall short. BioConnect extends physical security to digital applications, ensuring that only verified employees can access critical company data—no matter where they are.

Secure your critical infrastructure and sensitive areas.
Data centers, R&D labs, and executive offices require trusted identity verification beyond keycards. BioConnect Mobile Authenticator offers biometric-based access control to prevent breaches and ensure compliance.

Meet stringent security regulations effortlessly.
Hospitals and pharmaceutical companies handle sensitive materials that require strict access control. BioConnect enables biometric authentication for restricted areas, helping organizations comply with HIPAA and other regulations while eliminating keycard-related risks.
HID Mobile Credential
The BioConnect HID Mobile Credential allows any organization to implement and ensure trusted access for all their physical security needs. Unlock any HID Mobile Access compatible door with the BC Mobile Authenticator app. Add biometric authentication or a simple yes/no to your existing HID devices.


Leverage 3rd Party Applications
Already using a digital authenticator? No problem. With BioConnect, your enterprise can use existing identity providers like DUO, Ping ID, and Okta to authenticate at the door—bridging the gap between digital and physical security.
Why BioConnect?
Biometric Identity Assurance
Go beyond passwords and keycards with AI-driven facial authentication that verifies the user, not just the device.
Compliance Made Easy
Effortlessly meet security regulations with real-time access logs. BioConnect tracks every authentication event to simplify audits and ensure compliance with PCI-DSS, SOC 2, and more.
Frictionless User Experience
Enable fast, secure authentication with mobile push notifications and biometric approvals—ensuring security without slowing down operations.
Unlock the future of secure access.
Take control of your security with biometric and mobile-first authentication. See how BioConnect can secure your doors, networks, and digital assets.





